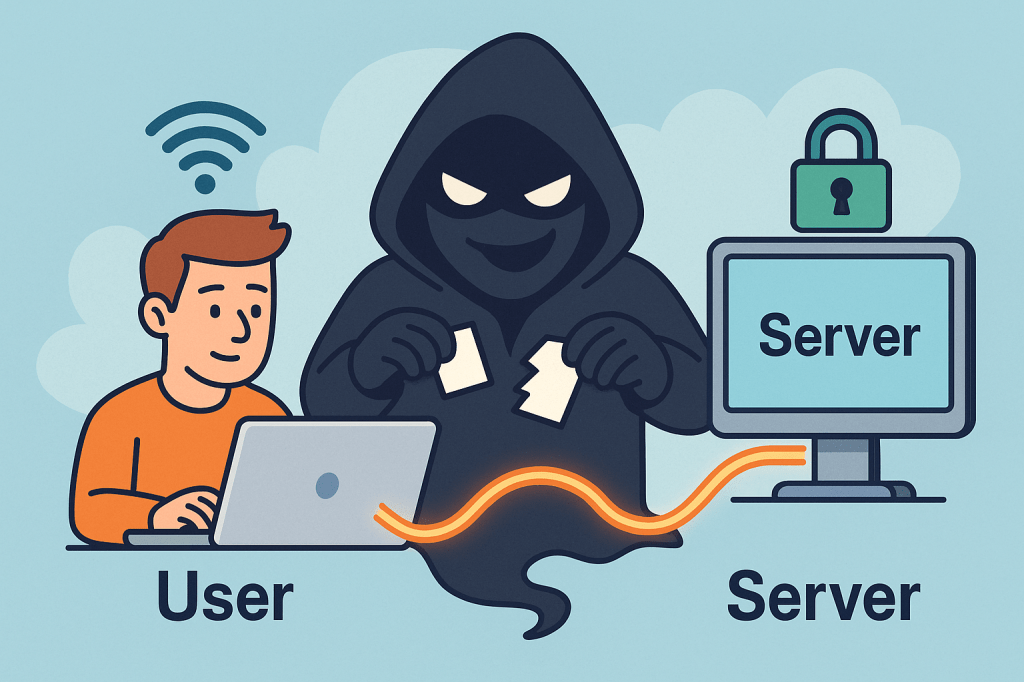
A Man-in-the-Middle (MITM) attack is when a third party secretly intercepts, reads, and possibly alters the communication between two parties who believe they are talking directly to each other. Think of it as someone quietly sitting between two people on a phone call, listening, possibly changing words, and passing the altered conversation on.
How MITM attacks work ?
A MITM attack has two essential parts: interception and optionally manipulation.
1) Interception (how the attacker gets between you and the other party)
The attacker places themselves on the network path so traffic sent from A → B goes through the attacker first. Common interception vectors (conceptual descriptions only):
- Rogue Wi-Fi / Evil twin: attacker sets up a fake Wi-Fi hotspot with a convincing SSID (e.g., “CoffeeShop_WiFi”). Users connect and all traffic goes through the attacker’s machine.
- ARP spoofing / ARP poisoning (local networks): attacker sends fake ARP messages on a LAN so traffic for the router or for another host is directed to the attacker’s NIC.
- DNS spoofing / DNS cache poisoning: attacker poisons DNS responses so a domain name resolves to an IP address the attacker controls.
- Compromised routers, proxies, or ISPs: if a router or upstream provider is compromised or misconfigured, traffic can be intercepted at that point.
- BGP hijacking (on the internet backbone): attacker manipulates routing announcements to direct traffic over infrastructure they control.
- Compromised certificate authorities or weak TLS setups: attacker abuses trust in certificates to intercept “secure” connections.
Important: the above are conceptual descriptions to help you understand how interception happens. I’m not providing exploit steps or tools to carry them out.
2) Manipulation (what the attacker can do with intercepted traffic)
Once traffic passes through the attacker, they can:
- Eavesdrop — read plaintext communication (passwords, messages, session cookies).
- Harvest credentials — capture login forms and credentials.
- Modify data in transit — change web pages, inject malicious scripts, alter transactions.
- Session hijack — steal session cookies or tokens to impersonate a user.
- Downgrade connections — force a downgrade from HTTPS to HTTP or strip TLS (SSL stripping) if possible.
- Impersonate endpoints — present fake certificates or proxy TLS connections to hide themselves.
Typical real-world scenarios / examples
- You connect to “FreeAirportWiFi” and a fake hotspot captures your login to a webmail service.
- On a corporate LAN, an attacker uses ARP spoofing to capture internal web traffic and collect session cookies.
- DNS entries for a banking site are poisoned so users are sent to a look-alike site where credentials are harvested.
- A corporate TLS-intercepting proxy (legitimate in some orgs) inspects HTTPS traffic — if misconfigured or if certificates are not validated correctly, this can be abused.
What’s the issue and how can MITM affect us?
MITM attacks threaten confidentiality, integrity, and authenticity:
- Confidentiality breach: private messages, PII, payment details, health records can be exposed.
- Credential theft & account takeover: stolen passwords or tokens lead to fraud, identity theft, or account compromises.
- Financial loss / fraud: attackers can alter payment instructions (e.g., change bank account numbers).
- Supply-chain or software tampering: updates or downloads could be altered.
- Reputation and legal risk: businesses can lose user trust and face compliance issues if customer data is intercepted.
Small, everyday examples (end-user impact): stolen email logins, unauthorized purchases, unauthorized access to corporate systems. For organizations: data breach notifications, regulatory fines, and remediation costs.
How to prevent Man-in-the-Middle attacks — practical, defensible steps
Below are layered, defense-in-depth controls: user practices, network configuration, application design, and monitoring.
A. User & device best practices
- Avoid public/untrusted Wi-Fi: treat public Wi-Fi as untrusted. If you must use it, use a reputable VPN.
- Prefer mobile/cellular networks when doing sensitive transactions if a trusted Wi-Fi is not available.
- Check HTTPS / certificate details for sensitive sites: browsers show padlock and certificate information (issuer, valid dates). If warnings appear, do not proceed.
- Use Multi-Factor Authentication (MFA): even if credentials are stolen, MFA adds a barrier.
- Keep devices patched: OS, browser, and app updates close known vulnerabilities attackers exploit.
- Use reputable endpoint security (antivirus/EDR) that can detect suspicious network drivers or proxying.
B. Network & infrastructure controls
- Use WPA2/WPA3 and strong Wi-Fi passwords; disable open Wi-Fi for business networks unless behind secure gateways.
- Harden DNS: use DNSSEC where possible and validate DNS responses; consider DNS over HTTPS (DoH) or DNS over TLS (DoT) for clients.
- Deploy network segmentation and limit broadcast domains (reduces ARP spoofing exposure).
- Use secure routing practices and monitor BGP for suspicious route changes (for large networks / ISPs).
- Disable unnecessary proxying and block rogue DHCP servers on internal networks.
C. TLS / application-level protections
- Enforce HTTPS everywhere: redirect HTTP → HTTPS and ensure all resources load over HTTPS to avoid mixed-content issues.
- Use HSTS (HTTP Strict Transport Security) with preload when appropriate — forces browsers to only use HTTPS for your domain.
- Enable OCSP stapling and certificate transparency: reduces chances of accepting revoked/forged certs.
- Prefer modern TLS versions and ciphers; disable older, vulnerable protocols (SSLv3, TLS 1.0/1.1).
- Certificate pinning (in mobile apps or critical clients) — binds an app to a known certificate or public key to prevent forged certificates (use cautiously; requires careful update procedures).
- Mutual TLS (mTLS) for machine-to-machine or internal high-security services — both sides verify certificates.
- Use strong authentication and short-lived tokens for APIs; avoid relying solely on long-lived session cookies without binding.
D. Organizational policies & monitoring
- Use enterprise VPNs for remote workers, with two-factor auth and endpoint posture checks.
- Implement Intrusion Detection / Prevention (IDS/IPS) and network monitoring to spot ARP anomalies, rogue DHCP servers, unusual TLS/HTTPS flows, or unexpected proxying.
- Log and review TLS handshakes, certs presented, and network flows — automated alerts for anomalous certificate issuers or frequent certificate changes.
- Train users to recognize fake Wi-Fi, phishing, and certificate warnings.
- Limit administrative privileges — reduce what an attacker can access with stolen credentials.
- Adopt secure SDLC practices: ensure apps validate TLS, implement safe error handling, and do not suppress certificate validation during testing.
E. App developer guidance (to make MITM harder)
- Never disable certificate validation in client code for production.
- Implement certificate pinning where appropriate, with a safe update path (e.g., pin several keys or allow a backup).
- Use OAuth / OpenID best practices (use PKCE for public clients).
- Use secure cookie flags (
Secure,HttpOnly,SameSite) and short session lifetimes. - Prefer token revocation and rotation; make stolen tokens short-lived.
Detecting a possible MITM (signs to watch for)
- Browser security warnings about invalid certificates, untrusted issuers, or certificate name mismatches.
- Frequent or unexpected TLS/HTTPS certificate changes for the same site.
- Unusually slow connections or pages that change content unexpectedly.
- Login failures that occur only on a certain network (e.g., at a coffee shop).
- Unexpected prompts to install root certificates (red flag — don’t install unless from your trusted IT).
- Repeated authentication prompts where you’d normally remain logged in.
If you suspect a MITM:
- Immediately disconnect from the network (turn off Wi-Fi/cable).
- Reconnect using a trusted network (e.g., mobile tethering) or VPN.
- Change critical passwords from a trusted network.
- Scan your device for malware.
- Notify your org’s security team and preserve logs if possible.
Quick checklist you can use / share
- Use HTTPS everywhere (HSTS, OCSP stapling)
- Enforce MFA across accounts
- Don’t use public Wi-Fi for sensitive tasks; if you must, use VPN
- Keep software and certificates up to date
- Enable secure cookie flags and short sessions
- Monitor network for ARP/DNS anomalies and certificate anomalies
- Train users on Wi-Fi safety & certificate warnings
Short FAQ
Q: Is HTTPS enough to prevent MITM?
A: HTTPS/TLS dramatically reduces MITM risk if implemented and validated correctly. However, misconfigured TLS, compromised CAs, or users ignoring browser warnings can still enable MITM. Combine TLS with HSTS, OCSP stapling, and client-side checks for stronger protection.
Q: Can a corporate proxy cause MITM?
A: Some corporate proxies intentionally intercept TLS for inspection (they present their own certs to client devices that have a corporate root installed). That’s legitimate in many organizations but must be clearly controlled, configured, and audited. Misconfiguration or abuse could be risky.
Q: Should I use certificate pinning in my web app?
A: Pinning helps but requires careful operational planning to avoid locking out users when certs change. For mobile apps and sensitive connections, pinning to a set of public keys (not single cert) and having a backup plan is common.
Recent Comments