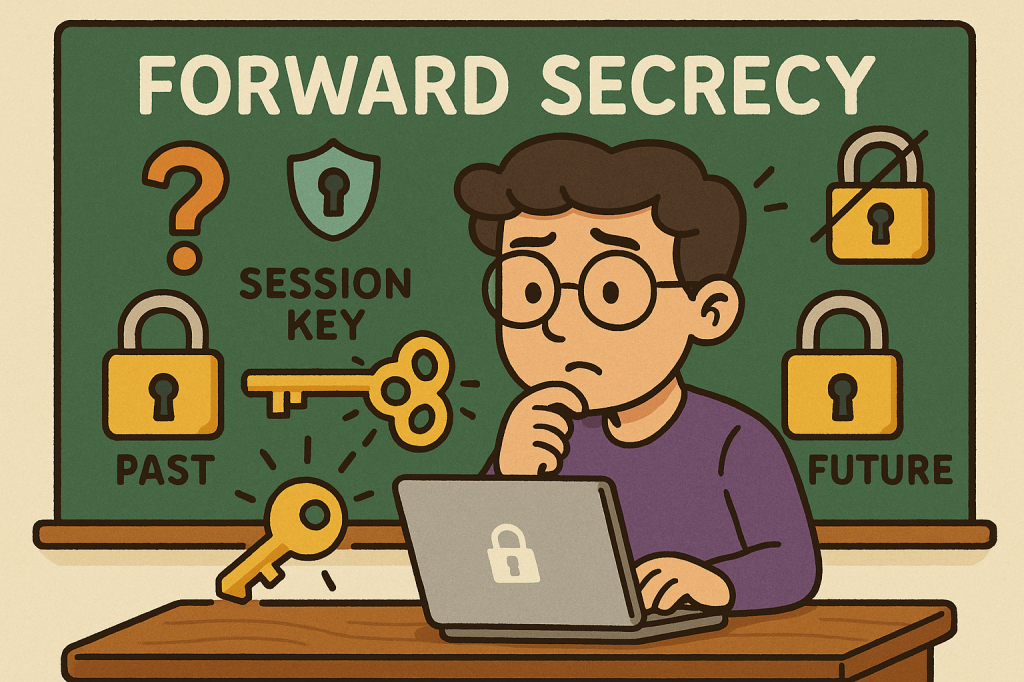
What is Forward Secrecy?
Forward Secrecy (also called Perfect Forward Secrecy or PFS) is a cryptographic property that ensures the confidentiality of past communications even if the long-term private keys of a server are compromised in the future.
In simpler terms: if someone records your encrypted traffic today and later manages to steal the server’s private key, forward secrecy prevents them from decrypting those past messages.
This makes forward secrecy a powerful safeguard in modern security protocols, especially in an age where data is constantly being transmitted and stored.
A Brief History of Forward Secrecy
The concept of forward secrecy grew out of concerns around key compromise and long-term encryption risks:
- 1976 – Diffie–Hellman key exchange introduced: Whitfield Diffie and Martin Hellman presented a method for two parties to establish a shared secret over an insecure channel. This idea laid the foundation for forward secrecy.
- 1980s–1990s – Early SSL/TLS protocols: Early versions of SSL/TLS encryption primarily relied on static RSA keys. While secure at the time, they did not provide forward secrecy—meaning if a private RSA key was stolen, past encrypted sessions could be decrypted.
- 2000s – TLS with Ephemeral Diffie–Hellman (DHE/ECDHE): Forward secrecy became more common with the adoption of ephemeral Diffie–Hellman key exchanges, where temporary session keys were generated for each communication.
- 2010s – Industry adoption: Companies like Google, Facebook, and WhatsApp began enforcing forward secrecy in their security protocols to protect users against large-scale data breaches and surveillance.
- Today: Forward secrecy is considered a best practice in modern cryptographic systems and is a default in most secure implementations of TLS 1.3.
How Does Forward Secrecy Work?
Forward secrecy relies on ephemeral key exchanges—temporary keys that exist only for the duration of a single session.
The process typically works like this:
- Key Agreement: Two parties (e.g., client and server) use a protocol like Diffie–Hellman Ephemeral (DHE) or Elliptic-Curve Diffie–Hellman Ephemeral (ECDHE) to generate a temporary session key.
- Ephemeral Nature: Once the session ends, the key is discarded and never stored permanently.
- Data Encryption: All messages exchanged during the session are encrypted with this temporary key.
- Protection: Even if the server’s private key is later compromised, attackers cannot use it to decrypt old traffic because the session keys were unique and have been destroyed.
This contrasts with static key exchanges, where a single private key could unlock all past communications if stolen.
Benefits of Forward Secrecy
Forward secrecy offers several key advantages:
- Protection Against Key Compromise: If an attacker steals your long-term private key, they still cannot decrypt past sessions.
- Data Privacy Over Time: Even if adversaries record encrypted traffic today, it will remain safe in the future.
- Resilience Against Mass Surveillance: Prevents large-scale attackers from retroactively decrypting vast amounts of data.
- Improved Security Practices: Encourages modern cryptographic standards such as TLS 1.3.
Example:
Imagine an attacker records years of encrypted messages between a bank and its customers. Later, they manage to steal the bank’s private TLS key.
- Without forward secrecy: all those years of recorded traffic could be decrypted.
- With forward secrecy: the attacker gains nothing—each past session had its own temporary key that is now gone.
Weaknesses and Limitations of Forward Secrecy
While forward secrecy is powerful, it is not without challenges:
- Performance Overhead: Generating ephemeral keys requires more CPU resources, though this has become less of an issue with modern hardware.
- Complex Implementations: Incorrectly implemented ephemeral key exchange protocols may introduce vulnerabilities.
- Compatibility Issues: Older clients, servers, or protocols may not support DHE/ECDHE, leading to fallback on weaker, non-forward-secret modes.
- No Protection for Current Sessions: If a session key is stolen during an active session, forward secrecy cannot help—it only protects past sessions.
Why and How Should We Use Forward Secrecy?
Forward secrecy is a must-use in today’s security landscape because:
- Data breaches are inevitable, but forward secrecy reduces their damage.
- Cloud services, messaging platforms, and financial institutions handle sensitive data daily.
- Regulations and industry standards increasingly recommend or mandate forward secrecy.
Real-World Examples:
- Google and Facebook: Enforce forward secrecy across their HTTPS connections to protect user data.
- WhatsApp and Signal: Use end-to-end encryption with forward secrecy, ensuring messages cannot be decrypted even if long-term keys are compromised.
- TLS 1.3 (2018): The newest version of TLS requires forward secrecy by default, pushing the industry toward safer encryption practices.
Integrating Forward Secrecy into Software Development
Here’s how you can adopt forward secrecy in your own development process:
- Use Modern Protocols: Prefer TLS 1.3 or TLS 1.2 with ECDHE key exchange.
- Update Cipher Suites: Configure servers to prioritize forward-secret cipher suites (e.g.,
ECDHE_RSA_WITH_AES_256_GCM_SHA384). - Secure Messaging Systems: Implement end-to-end encryption protocols that leverage ephemeral keys.
- Code Reviews & Testing: Ensure forward secrecy is included in security testing and DevSecOps pipelines.
- Stay Updated: Regularly patch and upgrade libraries like OpenSSL, BoringSSL, or GnuTLS to ensure forward secrecy support.
Conclusion
Forward secrecy is no longer optional—it is a critical defense mechanism in modern cryptography. By ensuring that past communications remain private even after a key compromise, forward secrecy offers long-term protection in an increasingly hostile cyber landscape.
Integrating forward secrecy into your software development process not only enhances security but also builds user trust. With TLS 1.3, messaging protocols, and modern encryption libraries, adopting forward secrecy is easier than ever.
Recent Comments